How Fast does your IT Support React?
If you ever think about this, you would probably think an “in-house” IT team or…
Looking For IT Support You Can Rely On?
With the addition of recent team members who are now fully trained in our ways…
Who sees your research data?
Many companies use university students to conduct research for them and the students sometimes use…
A Geek Father’s Day – Sunday, 16 June 2019
I did a Geek Mother’s Day – so it only seemed fair to do the…
Bot Blogging or Blog Botting?
You may have heard of the word processing addon “Grammarly” if you watch a lot…
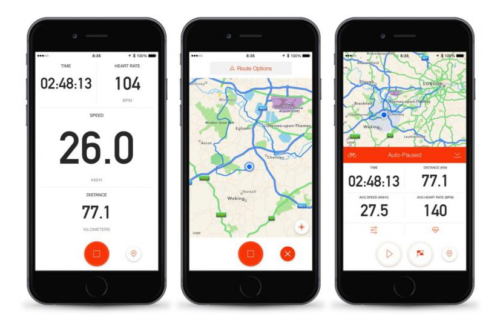
Loving My Cycle Tech
Working in remote tech support means spending a large part of my day sat at…
Data Privacy and Security Seminar – the one that you cannot miss this year
It’s almost a year since the General Data Protection Regulation (GDPR) came into effect and…
How to Create a Strong Password
“So I can’t win then, can I? It sounds like you want my passwords to…
Factors that impact on a password strength (Section 2)
Any password that is a word, is in the crackers dictionary, and all words of…
Factors that impact on a password strength (Section 1)
In our previous blog I introduced three factors that result in a password strength. Here…
Ways of stealing your password and top tips to stay safe
There are many ways of stealing a password, but the two main ways traditionally are:…
Your password is bad, and you should feel bad – accessibility vs security
Almost all of you will currently be using far too few passwords, most of which…
Data privacy and security seminar
So, you put locks on filling cabinets and rent safety deposit box at your bank?…
Do you want snooping with that latte?
Advice for businesses that are out and about, but advice that is just as useful…
Fishing Season is Out but Vishing Season is in
We’ve all heard of phishing, and you may know that it is the reason for…